Top Stories
Perplexity Faces Off Against SquareX Over Comet Browser Claims

URGENT UPDATE: Perplexity has vehemently denied recent allegations from cybersecurity firm SquareX, which claims that its Comet browser harbors a critical vulnerability. The controversy centers around the alleged hidden MCP API that SquareX says could allow for unauthorized command execution on users’ devices.
In a statement released earlier today, Perplexity labeled SquareX’s claims as “entirely false” and part of a larger trend of “fake security research.” The company emphasized that the alleged vulnerability requires user consent, developer mode activation, and manual sideloading of any malicious software.
SquareX’s report, which has prompted significant media attention, asserts that the MCP API found within Comet could enable local command execution without proper restrictions. This API, according to SquareX, allows embedded extensions to execute arbitrary commands, a functionality traditional browsers do not support.
“This poses a serious risk if someone were to compromise the Perplexity site,” Kabilan Sakthivel, a researcher at SquareX, stated. The implications of such a breach could potentially expose users’ devices to significant threats.
In response, Perplexity spokesperson Jesse Dwyer stated,
“To replicate this, the human user must turn on developer mode and manually sideload malware into Comet.”
He further asserted that user consent is always required for local MCP access, countering SquareX’s claims about the hidden nature of the API.
Perplexity contended that the API’s use is transparent and user-driven, stating,
“When installing local MCPs, we require user consent—users are the ones setting it up and calling the MCP API.”
Dwyer criticized SquareX’s methodology, alleging that the firm did not follow standard security reporting protocols.
In a surprising twist, SquareX claims that Perplexity executed a “silent update” to Comet shortly after their proof-of-concept was revealed. The update reportedly disabled the local MCP functionality, validating SquareX’s concerns about the browser’s security. SquareX asserts that three external researchers were able to replicate the vulnerability, which Perplexity has now addressed.
“This is excellent news from a security perspective,” SquareX concluded, noting that their research has contributed to improving the safety of the AI browser. They expressed disappointment that Perplexity did not respond to their initial vulnerability disclosure submission.
As the situation develops, users of the Comet browser are urged to stay informed about any updates from Perplexity regarding security measures. The ongoing dispute highlights the critical need for transparency and accountability in cybersecurity practices.
Stay tuned for further updates on this pressing issue as both companies continue to navigate the fallout from these significant claims.
-

 Top Stories1 month ago
Top Stories1 month agoUrgent Update: Tom Aspinall’s Vision Deteriorates After UFC 321
-
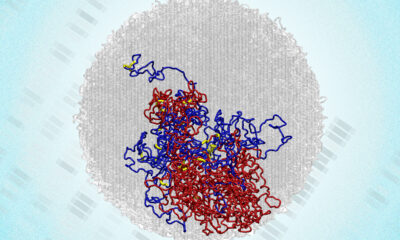
 Health2 months ago
Health2 months agoMIT Scientists Uncover Surprising Genomic Loops During Cell Division
-

 Science4 weeks ago
Science4 weeks agoUniversity of Hawaiʻi Joins $25.6M AI Project to Enhance Disaster Monitoring
-

 Top Stories1 month ago
Top Stories1 month agoAI Disruption: AWS Faces Threat as Startups Shift Cloud Focus
-

 Science2 months ago
Science2 months agoTime Crystals Revolutionize Quantum Computing Potential
-

 World2 months ago
World2 months agoHoneywell Forecasts Record Business Jet Deliveries Over Next Decade
-

 Entertainment2 months ago
Entertainment2 months agoDiscover the Full Map of Pokémon Legends: Z-A’s Lumiose City
-

 Top Stories2 months ago
Top Stories2 months agoGOP Faces Backlash as Protests Surge Against Trump Policies
-

 Entertainment2 months ago
Entertainment2 months agoParenthood Set to Depart Hulu: What Fans Need to Know
-

 Politics2 months ago
Politics2 months agoJudge Signals Dismissal of Chelsea Housing Case Citing AI Flaws
-

 Sports2 months ago
Sports2 months agoYoshinobu Yamamoto Shines in Game 2, Leading Dodgers to Victory
-

 Health2 months ago
Health2 months agoMaine Insurers Cut Medicare Advantage Plans Amid Cost Pressures








